How do I turn off HTTP Strict Transport Security?
how to use sites that use HTTP Strict Transport Security (HSTS) on Localhost?
Solution
I’m replying to my thread because the original note obliterated the formatting of my list o’ steps. So here they are again, hopefully in a much nicer-looking list:
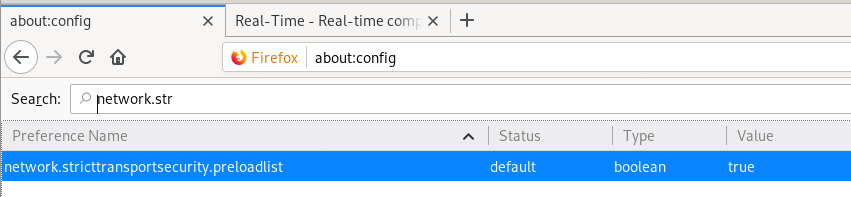
- Open a new window in Firefox and type “about:config” without the quotes and hit enter
- Confirm that you want to continue
- In the search field, type in
network.stricttransportsecurity.preloadlist
and hit enter – you’ll be left with one field
- If it’s marked as “true” then double-clicking it should turn it to “false”
- Close the window, then go back to your domain gTLD.
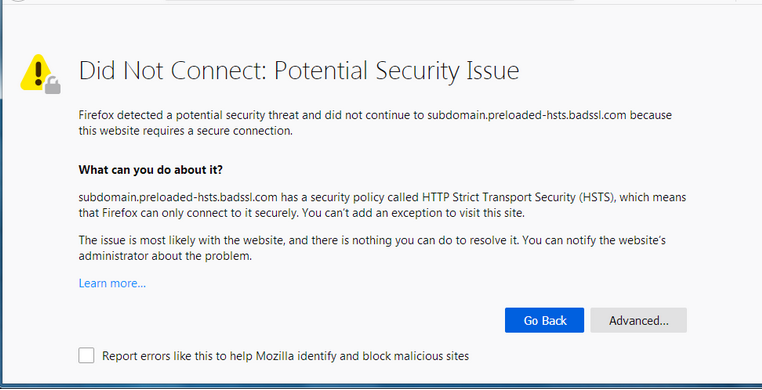
What is HTTP Strict-Transport-Security?
If a website accepts a connection through HTTP and redirects to HTTPS, visitors may initially communicate with the non-encrypted version of the site before being redirected, if, for example, the visitor types http://www.foo.com/ or even just foo.com. This protection creates an opportunity for a man-in-the-middle attack. The redirect could be exploited to direct visitors to a malicious site instead of the secure version of the original site.
The HTTP Strict Transport Security header informs the browser that it should never load a site using HTTP and should automatically convert all attempts to access the site using HTTP to HTTPS requests instead.
Note: The Strict-Transport-Security header is ignored by the browser when your site is accessed using HTTP; this is because an attacker may intercept HTTP connections and inject the header or remove it. When your website is accessed over HTTPS with no certificate errors, the browser knows your site is HTTPS capable and will honor the Strict-Transport-Security header.
more information here.
Preloaded HSTS sites
There is still a window where a user who has a fresh install, or who wipes out their local state, is vulnerable. Because of that, Chrome maintains an “HSTS Preload List” (and other browsers maintain lists based on the Chrome list). These domains will be configured with HSTS out of the box.
If you own a site that you would like to see included in the preloaded HSTS list you can submit it at https://hstspreload.org.
A selected subset of the members of the preloaded HSTS list:
- Paypal
- Simple
- Linode
- Stripe
- Lastpass
Check the source for the full list.